Infiltrating the EVM-I: Demystifying Smart Contracts & Auditing comprises of information about compilation breakdown of solidity code, the vulnerable components of blockchain ecosystem and how Smart contract auditing is crucial.
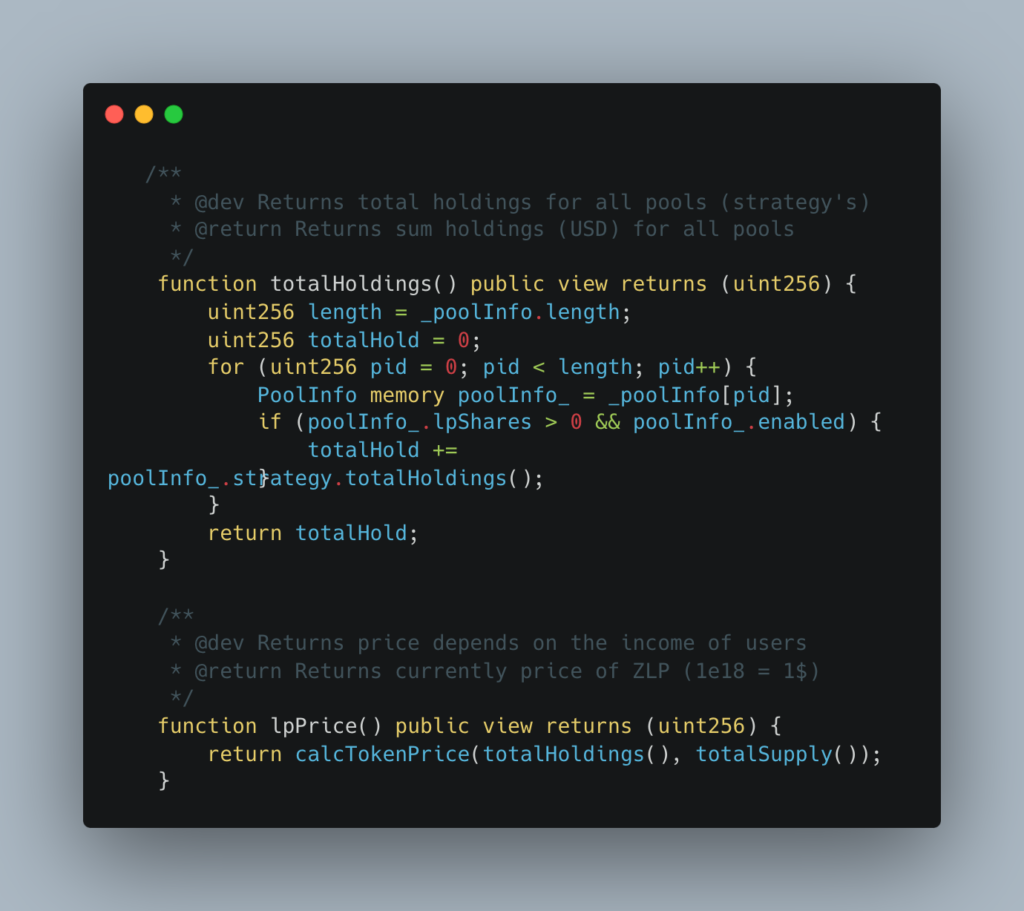
Zunami is a decentralized protocol operating in the Web3 space, specializing in issuing aggregated stablecoins like UZD and zETH. These stablecoins are generated from omnipools that employ various profit-generating strategies. Recently, the protocol was exploited, resulting in a loss of $2.1M. The exploit specifically targeted Zunami's UZD and zETH liquidity pools on the Curve ecosystem. This analysis delves into the impact and mechanisms for this kind of vulnerability.
The Zunami Protocol experienced a severe price manipulation attack that led to a loss of approximately $2.1M. The attacker was able to exploit Zunami’s zETH and UZD liquidity pools on the Curve platform. This caused the zStables (zETH and UZD) to depeg dramatically - zETH by 85% and UZD by 99%.
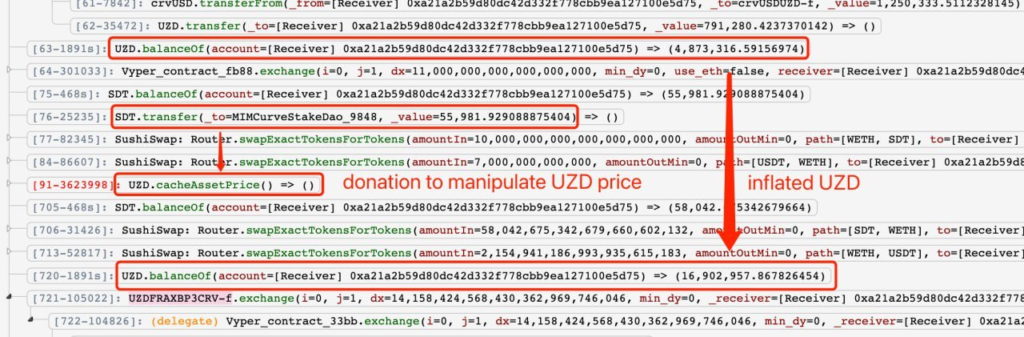
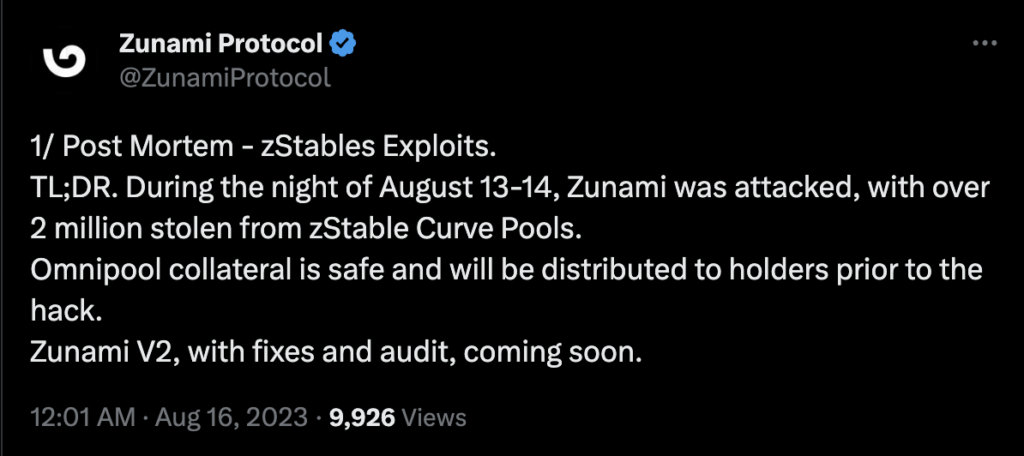
The Zunami Protocol hack serves as a cautionary tale about the risks and vulnerabilities present in complex decentralized financial systems. The exploitation capitalized on multiple weaknesses in Zunami's design, leading to a substantial loss of funds and trust. Given the growing number of such exploits, it's imperative for projects in the DeFi space to take robust security measures seriously, undergoing rigorous audits from a reputed audit firm like Blockapex and implementing strong protective mechanisms to shield both their assets and their user base.

Infiltrating the EVM-I: Demystifying Smart Contracts & Auditing comprises of information about compilation breakdown of solidity code, the vulnerable components of blockchain ecosystem and how Smart contract auditing is crucial.
Illiquid Marketplaces is a common problem with various underlying factors. Information asymmetry, where one party has more knowledge than the other, makes it challenging to establish agreements and facilitate transactions. Complex market structures, with intricate trading rules or inadequate infrastructure, can hinder liquidity. Small marketplaces with fewer users naturally have less liquidity. Fragmented marketplaces, where sellers impose rigid terms, create barriers for potential buyers.
On February 17, 2023, Platypus Finance was hacked, resulting in a loss of approximately $8.5 million worth of assets. In this hack analysis, we will delve into the details of the attack, the vulnerability that was exploited, and the impact it had on the platform and its users.
What was essentially the biggest hack in the history of cryptocurrency became a valuable lesson on the importance of security and just how powerless big organizations can become in the face of powerful hackers. The unusual trajectory of this incident also begs the question of where to place the blame in these kinds of attacks. Read more to find out exactly how the hack took place as we analyze the most pressing questions surrounding this attack.
BlockApex (Auditor) was contracted by Voirstudio (Client) for the purpose of conducting a Smart Contract Audit/Code Review of Unipilot Farming module. This document presents the findings of our analysis which took place on _9th November 2021___ .
The successful upgrade of the London Hard Fork is a big difference from the fork leading to Ethereum Classic that took place back in 2016. However, despite their divergence, both are milestones in the Ethereum world- guaranteed to have lasting impacts on the blockchain as we know it. Read more to find out the circumstances surrounding each hard fork and the role they may play in shaping Ethereum's future.
The last few years have resulted in consumer privacy and data breach issues. Those issues have made the users conscious and ambiguous about the data on the internet. Read more in this blog.
The purple team exercises allow for regular testing of controls to ensure they still function as expected. Combining red and blue functions also means that the blue team does not have to learn the red-team skills, or take the time to recreate attack behaviors themselves.
Lets understand the smart contract storage model in Ethereum and EVM-based chains and how you can access the public and private variables of any smart contract deployed on the blockchain. We can do this by using cast storage.


