Introduction
Yearn Finance is a well-known yield aggregator in the Decentralized Finance (DeFi) sector. It offers users, DAOs, and other protocols the opportunity to deposit digital assets and earn yield in return. Governed by YFI token holders and maintained by various independent developers, Yearn has a range of core products, such as Vaults, and a democratic governance system.
This analysis aims to explore and explain the Yearn Finance hack that took place on April 13, 2023. We aim to delve into the intricate details of this exploit to allow both non-technical and technical readers to understand the chain of events that led to the theft of approximately $11.4 million.
Hack Impact
The exploit on Yearn Finance occurred due to a misconfiguration in the yUSDT vault, leading to a loss of approximately $11.54 million. This vulnerability was exploited by the attackers, leading to a significant financial impact and highlighting a fundamental flaw in the system's architecture.
Yearn Finance Hack Explained
Step 1: Wallet Preparation and Funding
The attacker started by funding their wallet through Tornado Cash, a platform for transaction privacy on Ethereum. The exact details of the transaction remain obscured due to Tornado Cash's privacy-preserving features.
Step 2: Flash Loan Acquisition
After the funding, the attacker initiated a flash loan from the Aave platform, a lending protocol. This loan was large, encompassing 5 million DAI, 5 million USDC, and 2 million USDT.
Step 3: yUSDT Contract Manipulation
Following the acquisition of the flash loan, the attacker transferred these funds to the misconfigured yUSDT contract in Yearn Finance. Because of the wrong token dependency on iUSDC instead of the intended iUSDT, the contract erroneously minted a significant amount of yUSDT tokens to represent the newly deposited funds.
Step 4: Withdrawal and Rebalance
The attacker then redeemed their yUSDT tokens, effectively withdrawing all the assets from the Aave V1 vault. Then, they minted bZxUSDC tokens and sent them to the contract. By doing this, the attacker was able to manipulate the price of each share. A subsequent rebalance of the vault reduced the value of each yUSDT token to zero.
Step 5: Exploiting Misconfiguration
At this point, the attacker exploited the aforementioned misconfiguration. By depositing 1 wei (a tiny fraction of 1 Ether, similar to a cent in relation to a dollar) of USDT to the yUSDT contract, the misconfiguration allowed the attacker to mint over 1 quadrillion yUSDT tokens. This extreme minting was possible due to the low value of the yUSDT tokens, each essentially worth zero after the rebalance.
Step 6: Conversion and Payback
The attacker then proceeded to swap the wrongly minted yUSDT for USDT, USDC, and DAI tokens through Curve Finance pools. After obtaining these stablecoins, the attacker repaid the flash loan they had taken from Aave.
Step 7: Profit Extraction
After repaying the flash loan, the attacker effectively kept the remaining funds, totaling about $11.54 million in the form of stablecoins. This marked the end of the exploit.
The Misconfigured Fruit Stand: A Simple Analogy of the Yearn Finance Hack
Picture a bustling fruit stand that sells two types of fruit: apples and oranges. The fruit stand utilizes a sophisticated computer system to accurately track its inventory of each fruit type.
However, a critical mistake was made during the system setup: the barcode assigned for apples was mistakenly used for oranges. The consequence? Every time someone brings oranges to the stand, the system mistakenly recognizes and registers them as apples.
One day, a cunning customer (the attacker in our case) discovers this flaw. They borrow a massive amount of oranges and apples from another fruit stand (akin to taking a flash loan), and subsequently deposit them into the misconfigured fruit stand. The flawed system registers this transaction as a considerable influx of apples due to the barcode mix-up.
Subsequently, the system recalculates the value of each apple share based on the total quantity of apples - a quantity falsely inflated due to oranges being erroneously classified as apples. With the system perceiving an excessive stock of apples, the value of each apple share drops significantly.
Seizing this opportunity, the cunning customer deposits a single apple into the fruit stand (equivalent to 1 wei of USDT). Given the incredibly low value of each apple share (due to the miscount), the system grants the customer an enormous amount of apple shares in return.
Finally, the cunning customer sells these apple shares to other customers at the current market price, reaping a hefty profit. Concurrently, they return the borrowed fruits to the original stand (equivalent to repaying the flash loan), thus clearing their obligations while pocketing the gains from the apple shares sold.
In this analogy, the 'fruit stand' is representative of the yUSDT contract, 'apples' symbolize USDT, 'oranges' signify USDC, and 'apple shares' parallel yUSDT tokens. Just like the cunning customer who capitalized on the fruit stand's system flaw, the attacker in the Yearn Finance Hack exploited a misconfiguration to walk away with significant illicit profits.
Recommendations for Enhanced Security
This exploit could have been prevented with diligent validation and verification of the Fulcrum address before deployment. The deployer should have provided the correct address for the iUSDT token, not iUSDC, in the constructor.
It further underscores the importance of conducting comprehensive security reviews of deployment scripts to ensure all deployment parameters are correctly configured.
Transaction Analysis
The attack on Yearn Finance involved multiple addresses and transactions. The addresses and the transactions used in this exploit were:
Attacker Externally Owned Accounts (EOAs)
Attacker EOA-1: 0x5bac20beef31d0eccb369a33514831ed8e9cdfe0
Attacker EOA-2: 0x16Af29b7eFbf019ef30aae9023A5140c012374A5
Attacker EOA-3: 0x6f4A6262d06272c8B2E00Ce75e76d84b9D6F6aB8
Attacker Contract Accounts
Attacker Contract-1: 0x8102ae88c617deb2a5471cac90418da4ccd0579e
Attacker Contract-2: 0x9fcc1409b56cf235d9cdbbb86b6ad5089fa0eb0f
Victim Contract Account
Victim Contract: 0x83f798e925BcD4017Eb265844FDDAbb448f1707D
Attack Transactions:
First Transaction: 0xd55e43c1602b28d4fd4667ee445d570c8f298f5401cf04e62ec329759ecda95d
Second Transaction: 0x8db0ef33024c47200d47d8e97b0fcfc4b51de1820dfb4e911f0e3fb0a4053138
At the time of writing this analysis, the attacker holds around $9,817,782 across all the EOAs involved in this exploit.
Conclusion
The Yearn Finance hack is a stark reminder of the necessity of stringent smart contract auditing in the DeFi landscape. By exploiting a misconfiguration in the yUSDT vault, the attacker pilfered approximately $11.54 million, highlighting the risks associated with overlooking security checks.
Preventative measures, such as those offered by security firms like BlockApex, are crucial. Their meticulous smart contract audits can identify potential vulnerabilities and rectify them before deployment, ensuring the robustness of the DeFi platform.
The Yearn Finance incident underlines the importance of security diligence. Through rigorous audits and continuous attention to security, the DeFi community can look to build safer, more resilient systems for users and stakeholders alike.
 BlockApex
BlockApex  May 23, 2023
May 23, 2023 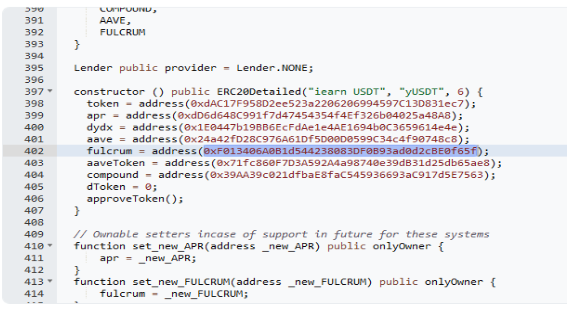

 BlockApex
BlockApex  August 25, 2021
August 25, 2021