Creating an internet owned by no one yet contributed to by everyone is bound to have problems related to security- something many believe that the builders of Web3 may not be equipped with.
Jimbo's Protocol is a decentralized finance (DeFi) system built on the Arbitrum chain. The protocol uses a semi-stable floor price for its ERC-20 token, $JIMBO, backed by a treasury of Ether (ETH). However, despite its pioneering efforts to maintain on-chain liquidity and price floors, Jimbo's Protocol recently faced a Flash loan attack. On May 28, 2023, a sophisticated attacker managed to exploit a loophole in the protocol's slippage control mechanism, walking away with approximately $7.5 million in ETH.
The attack had immediate and severe consequences for Jimbo's Protocol and its community. The attacker successfully drained a large portion of the treasury's ETH, affecting the protocol's stability and trustworthiness. The incident led to a sharp 40% decline in the value of $JIMBO, eroding the token's market position and investor confidence.
In decentralized finance (DeFi), liquidity rebalancing is the process of reallocating assets within a liquidity pool to ensure efficient capital utilization and smooth price discovery. In simple terms, it means making sure there's enough "money" in the right places in a trading pool to make trades easy and fair.
Slippage occurs when the price of an asset changes between the time you place an order and the time the order is fulfilled. In DeFi, it's particularly important to control slippage to prevent significant price fluctuations that could result from large trades.
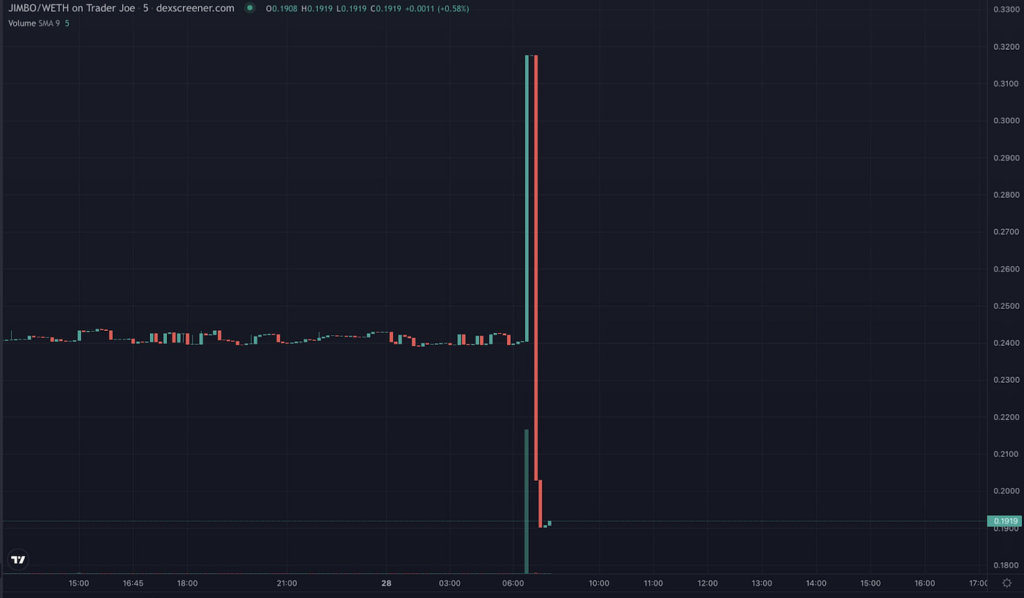
In $JIMBO's case, rebalancing happens via three primary functions: Shift(), Reset(), and Recycle(). These are triggered based on the state of different bins—Floor Bin, Active Bin, and Trigger Bin.
The Shift() function plays a crucial role in the $JIMBO protocol, automatically activating when the Active Bin (the pool bin where the current trading price resides) moves past the Trigger Bin. The function performs two primary actions:
Simultaneously, the Shift() function also invokes a Reset() function call to redistribute the remaining $JIMBO tokens within the pool.
For more comprehensive insights into how these bins operate within the protocol, please refer to this Link
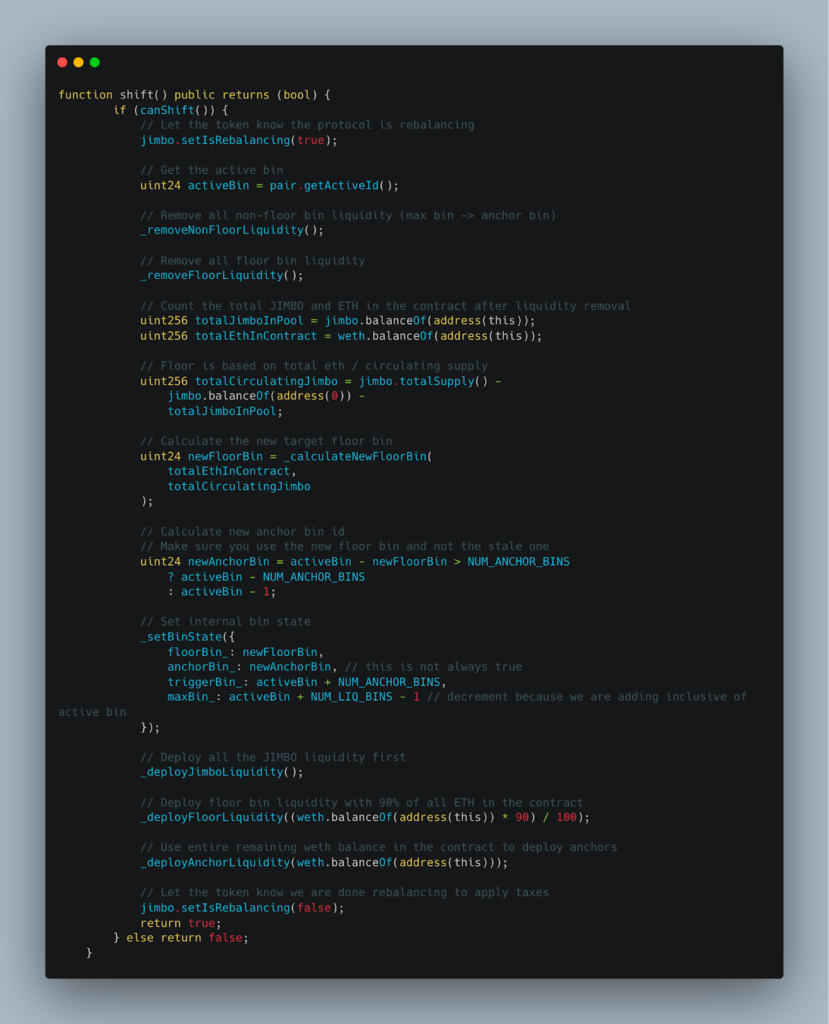
Step 1: Obtain Initial Funds
Step 2: Inflate $JIMBO Price
Step 3: Transfer Tokens to Contract
Step 4: Invoke Shift()
Step 5: Crash the Market Price
Step 6: Trigger Another Rebalance
Step 7: Exploit and Profit
The attacker then returns the initial ETH borrowed through the flash loan, retaining a substantial net gain of 7.5 million.
The critical flaw was the absence of slippage controls in the Shift() function, enabling the attacker to trigger rebalancing actions at artificial price levels. Once liquidity was redeployed at these inflated prices, the attacker could then manipulate the market to purchase tokens at a much lower cost, making a substantial profit in the process.
Attacker’s Address(ETH)
Notable Transactions:
JimboController Contract
Attack Transaction

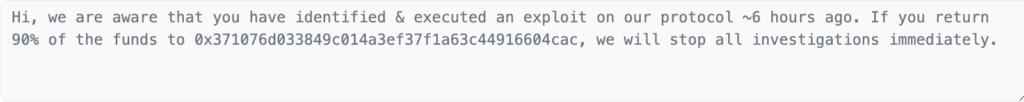
The protocol also sent an On chain message to the hacker
A system with a more sophisticated rebalancing mechanism that includes proper slippage control, could have likely prevented this exploit. By undergoing a comprehensive security audit, potentially from firms like BlockApex, protocols can identify and address these vulnerabilities before they're exploited.
The Jimbo Protocol incident serves as a cautionary tale that even innovative DeFi protocols are vulnerable to sophisticated attacks. This event highlights the importance of comprehensive security audits, a service that BlockApex specializes in, to identify and mitigate vulnerabilities in DeFi protocols. As the DeFi sector continues to evolve, so should its security measures to protect investor interests and maintain system integrity.

Creating an internet owned by no one yet contributed to by everyone is bound to have problems related to security- something many believe that the builders of Web3 may not be equipped with.
Security and privacy are among the top issues expected to arise in the metaverse. Some have even gone so far as to say that the metaverse is capitalizing on users' desire to escape from reality.
Data breaches and consumer privacy are one of the most alarming security issues in IT space. About 45% of the world’s population uses social media which makes approximately 3.48 billion people to be interacting with any kind of social media network. These tremendous amounts of connections can lead to various kinds of vulnerabilities if the data is gone into the wrong hands creating pretty damaging consequences.
The Dexible hack affected a total of 17 user accounts, with the majority of losses coming from a single address belonging to BlockTower Capital, a prominent investment firm.
Flower Fam is an NFT-based project, after you mint your NFT you can “harvest” them on weekly bases to get 60% royalties. It's quite simple: every flower has a 10% chance to win. The rarer the species of a flower.
Lets understand the smart contract storage model in Ethereum and EVM-based chains and how you can access the public and private variables of any smart contract deployed on the blockchain. We can do this by using cast storage.
The Deus DAO hack had significant financial consequences, with users collectively losing around $6.5 million across Arbitrum, BSC, and Ethereum chains. Furthermore, the hack caused the DEI stablecoin to depeg by more than 80%, destabilizing its value and potentially shaking investor confidence.
What was essentially the biggest hack in the history of cryptocurrency became a valuable lesson on the importance of security and just how powerless big organizations can become in the face of powerful hackers. The unusual trajectory of this incident also begs the question of where to place the blame in these kinds of attacks. Read more to find out exactly how the hack took place as we analyze the most pressing questions surrounding this attack.
Unipilot is an automated liquidity manager designed to maximize ”in-range” intervals for capital through an optimized rebalancing mechanism of liquidity pools. Unipilot V2 also detects the volatile behavior of the pools and pulls liquidity until the pool gets stable to save the pool from impairment loss.


